Power Automate implementation in a private cluster
On this page
This article explains the implementation of Power Automate workflows within a zero-trust architecture for the CluedIn application hosted in a private Azure Kubernetes cluster.
Prerequisites
In order to use Power Automate workflows in a zero-trust corporate environment, make sure you fulfill the following prerequisites:
-
Firewall Application rule FQDN –
api.flow.microsoft.com,*.api.crm4.dynamics.com,*.crm4.dynamics.com,graph.microsoft.com,api.powerapps.com,*.logic.azure.com -
Firewall Network rule – tag
Appservice.<region> -
Delegated subnet (Microsoft.App/environments) for Azure function with /26 IP range on your existing Vnet or a new one ( a new Vnet needs to be peered with AKS subnet).
Overview
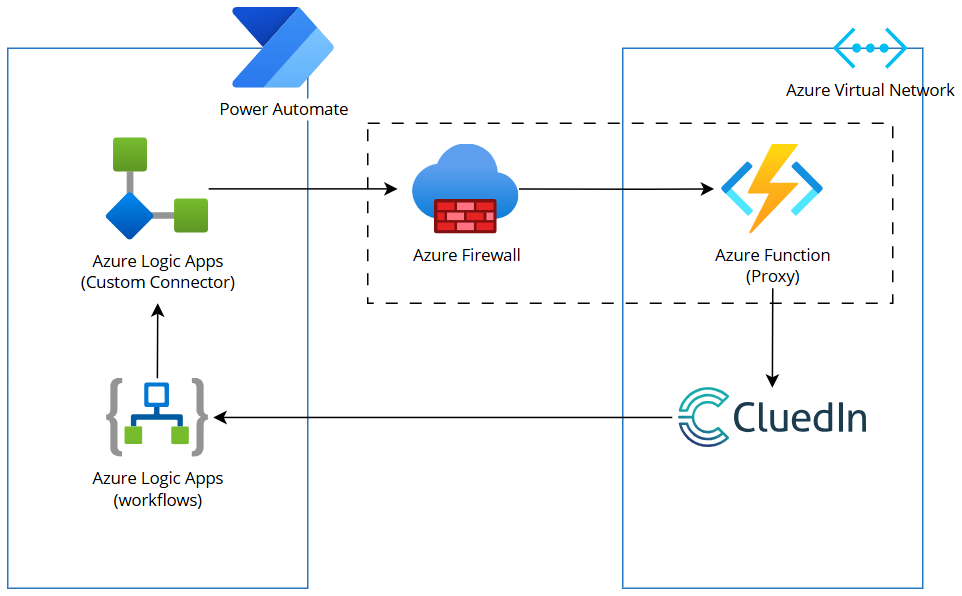
The solution ensures that incoming requests are securely proxied through an Azure Function and only accessible within a restricted IP range. This setup integrates Power Automate workflows using an Azure Logic Apps custom connector.
Network diagram
Sequence diagram
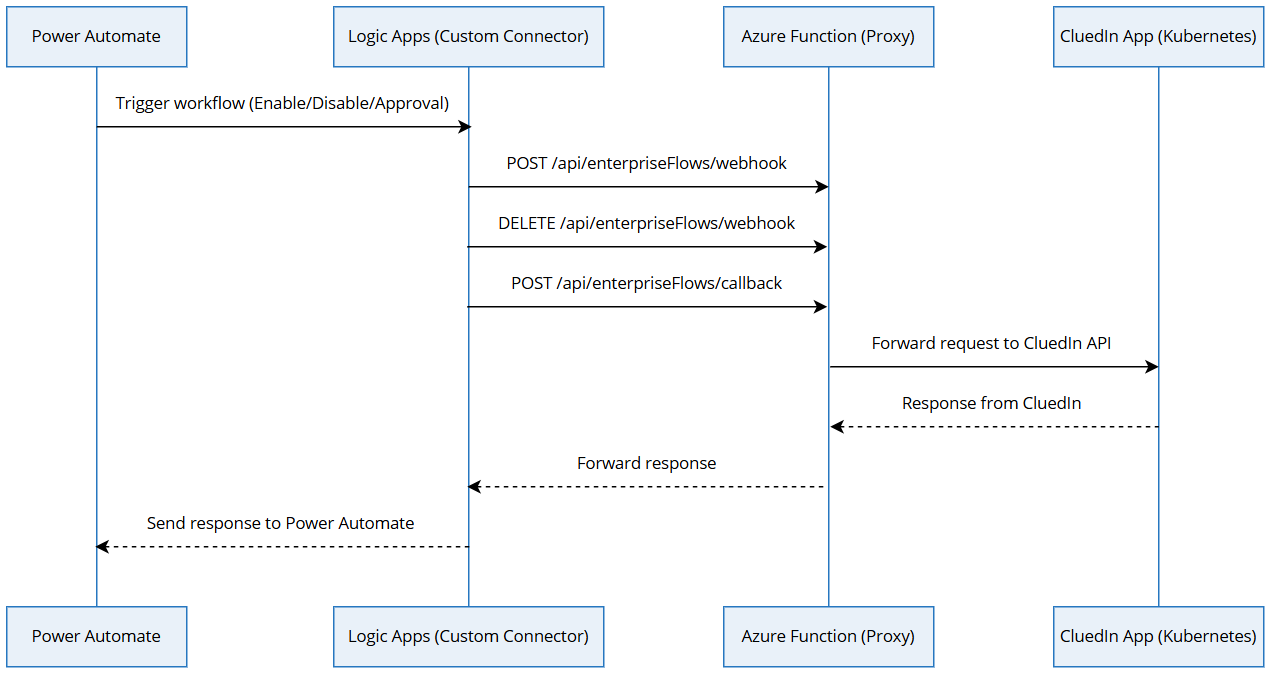
Request flow
- Power Automate invokes Logic Apps Custom Connector.
- Logic Apps Custom Connector sends the request to the Azure Function Proxy.
- Azure Function forwards the request to the CluedIn API.
- CluedIn processes the request and returns a response.
- Azure Function passes the response back to Power Automate.
Assumptions
- Azure Function does not need to handle any additional authentication or processing.
- There are no security policies that prevent the Azure Function from being installed.
- There are no security policies that prevent HTTP traffic to and from the Azure Function.
Steps
-
Create the Azure Function app in the same virtual network as CluedIn.
-
Upload the code (GitHub). To get access, contact our support at support@cluedin.com.
-
Under Networking > Public network access, restrict IP address to Service Group - Azure Connectors.
The following screenshot shows the Access Restrictions page in the Azure portal with the list of access restriction rules defined for the selected app.
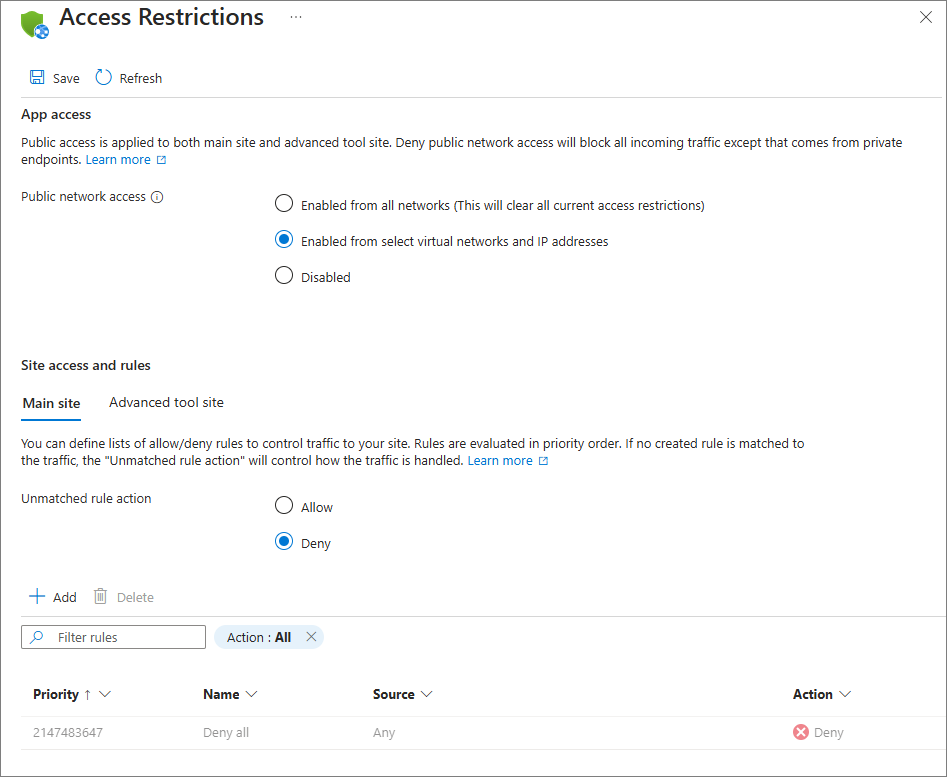
-
Set unmatched rule action to Deny.
-
Add a rule to restrict traffic from Azure Connectors.
Components
Azure Function App
- Acts as a proxy, forwarding requests to CluedIn.
- Passes headers and content without modification.
- Anonymous authentication mode.
- Azure Function is configured with an IP restriction to allow only Azure Connectors using service tags.
- Example for a Power Platform environment in Europe region:
AzureConnectors.NorthEuropeAzureConnectors.WestEuropeLogicApps.NorthEuropeLogicApps.WestEurope
Power Automate Custom Connector
- Custom connector is configured to send requests to the Azure Function Proxy.
- Uses the Azure Function as the host endpoint.
- Power Automate triggers:
- Calls CluedIn when a workflow is enabled or disabled.
- Sends approval responses to CluedIn.
- APIs called by Power Automate:
- Enable Workflow:
POST /api/enterpriseFlows/webhook - Disable Workflow:
DELETE /api/enterpriseFlows/webhook - Approval Response:
POST /api/enterpriseFlows/callback
- Enable Workflow: